Admin Dashboard ScaleEnterpriseSelf-Hosted
The Admin Dashboard provides a web UI to see various details of your Okteto instance in a centralized location and offers features for managing parts of the Okteto experience for your users.
You can access the Admin Dashboard by clicking on the Admin icon on the left sidebar.
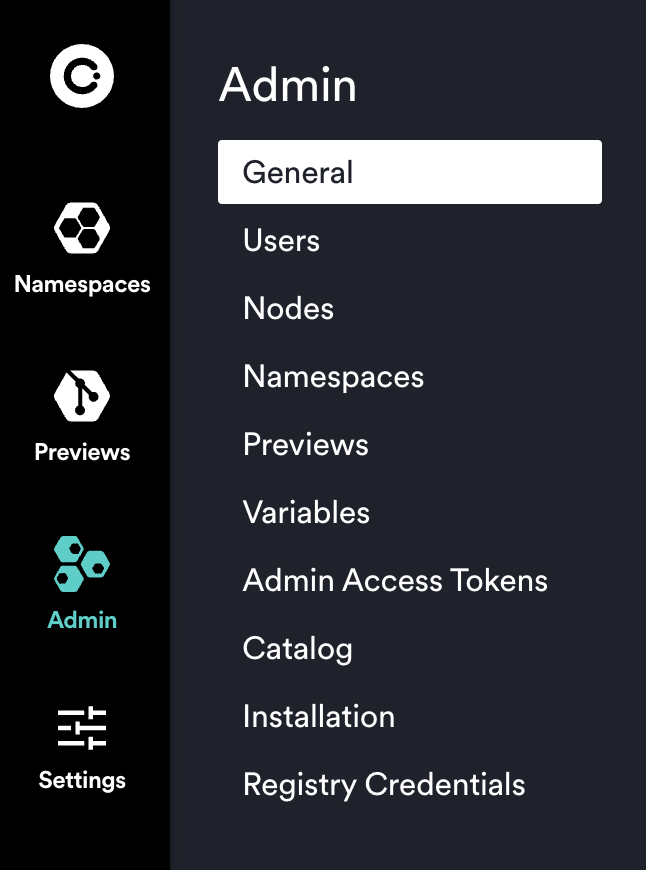
This Admin view consists of the following views currently:
- General
- Users
- Nodes
- Namespaces
- Previews
- Variables
- Admin Access Tokens
- Catalog
- Installation
- Registry Credentials
We will cover these in more detail below.
Accessing the dashboard
Only accounts with the administrator role will be able to access the Administration Dashboard. The first user signing up into your Okteto instance will automatically become the initial administrator.
You can promote other accounts to the administrator role in the Users section of the Admin Dashboard or by adding the dev.okteto.com/super: "true" label to the corresponding serviceAccount in Kubernetes.
General
The overview section of the Admin Dashboard is designed to give you a high level view of your entire Okteto instance. From here, you can drill down into more specific settings and details. This section currently shows you the following information:
- Your current pricing plan
- Okteto Helm chart version
- Okteto CLI version
- Expiration date of your license
- Number of available seats
- Number of nodes in your cluster
- Number of namespaces in your Okteto instance
- Number of preview environments currently active
- Git SSH key
- Autoscaler configuration
- Garbage Collector configuration
With the exception of the Settings section, this data is informative only. The Settings section contains a few configurable settings to help you customize your Okteto instance as necessary.
Users
From this section you can manage all users in your Okteto instance. This is a list of all users that have created an account in your Okteto instance, their respective roles, and with appropriate actions to manage their membership.
The User column is also the user's default namespace name/id. For example, a User value of "darryl" means that that user's namespace will also be called "darryl". Any additional namespaces created by "darryl" will show up only in the Namespaces tab.
On this page an administrator will be able to:
- View the total number of users on the Okteto instance (The
Totalvalue in the top right of the table) - View each user's name, email, and avatar
- View when a user was
Last Seen(any user who recently sent any API request to Okteto, e.g. from the browser, CLI, GitHub actions) - Change each user's role (Select
UserorAdminfrom the dropdown menu in theRolecolumn) - Remove users (Click the
(X) Remotebutton on the far right)
Removing the user will automatically remove all the namespaces owned by the deleted user.
Nodes
In this section of the Admin Dashboard, you can find the following system information about your Kubernetes cluster, separated by node:
- Number of running pods
- Number of volumes in use
- Memory utilization
- CPU utilization
Namespaces
This view enables you to manage all of the namespaces within your Okteto instance, including the ability to view (masquerade as the user), wake, or persist any namespace. The top of the namespace table also shows you the default settings for the garbage collection configuration.
For each namespace, an administrator can:
- View the name, owner, status (
ActiveorSleeping), and when it was last active - Get
read-onlyaccess to any namespace managed by Okteto (using theViewoption) - Manually wake the namespace (using the
Wake Namespaceoption) - Mark the namespace as
persistent(using theKeep Awakeoption) to exempt it from the garbage collection process
Previews
Similar to the namespaces section, the Previews section shows you a list of all Preview Environments that exist in your Okteto instance.
From this page, an administrator can view the default settings for the garbage collection configuration and view any of the listed preview environments.
This table provides a consolidated view about preview environments, including:
- Preview environment name
- Owner
- Scope (
PersonalorGlobal) - Status (
ActiveorSleeping) - Last seen
Variables
The Variables section of the Admin dashboard lets you define cluster-wide variables. You can refer to these variables directly in your Okteto manifest using the $SOME_VAR syntax. They are also injected into the environment running the commands in the deploy section of the manifest.
Variables defined by the user take precedence over variables and build secrets defined through the manifest.
We recommend using build secrets to inject sensitive data into your Dockerfile.
The example below shows how to configure your Okteto manifest to mount a local .env file into your Dockerfile:
build:
api:
context: .
secrets:
my_env: .env
You can refer to this secret from your Dockerfile using the syntax below:
RUN --mount=type=secret,id=my_env,target=/etc/secrets/.env cat /etc/secrets/.env
The content of the .env file would be:
${MY_PASSWORD}
where MY_PASSWORD can be a local environment variable or an Okteto Secret, and it gets subsituted by Okteto before mounting the file as a build secret.
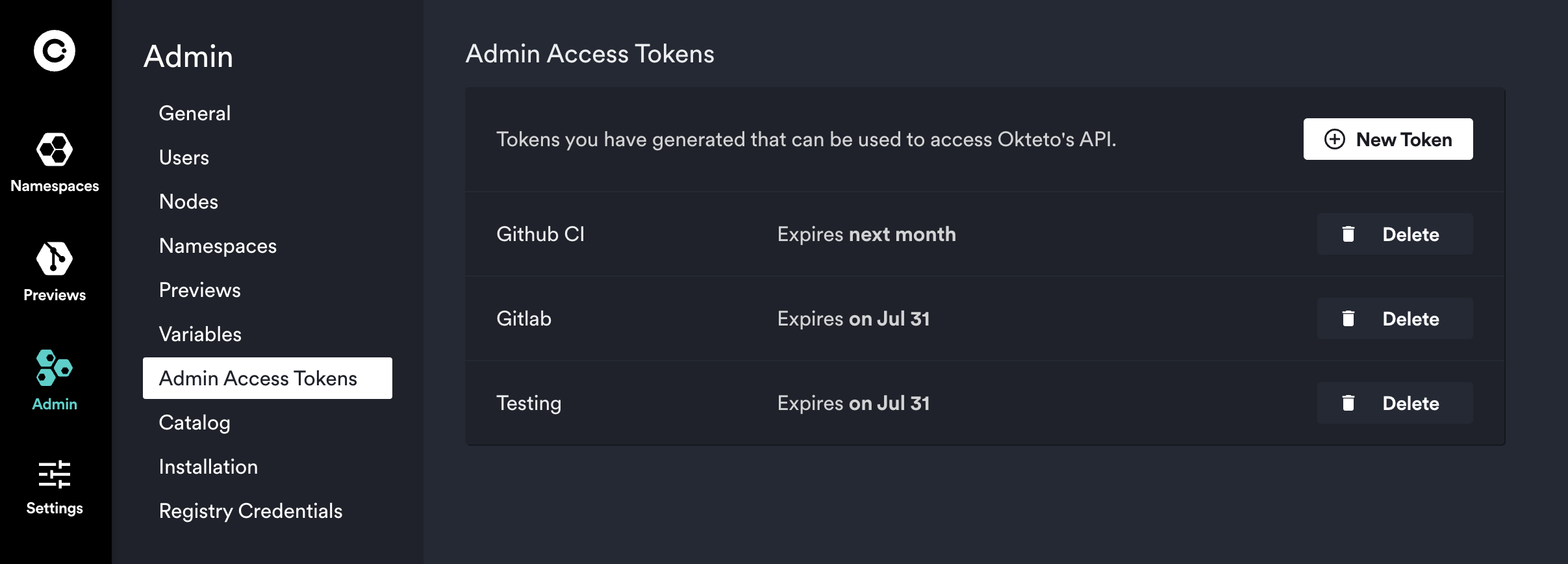
Admin Access Tokens
You can use Admin Access Tokens instead of OAuth to authenticate with Okteto.
Admin Access Tokens are created and work in the same manner as Personal Access Tokens, with the difference that they have admin permissions. They are intended to be used over personal access tokens for shared automations, e.g. Preview Environments.
Catalog
This section of the Admin dashboard enables you to create a catalog of pre-defined development environments for anyone in your Okteto instance to deploy quickly from their Deploy Dev Environment screen. You can reduce the amount of time it takes a developer to get up and running by defining these catalog entries so they're available for developers to select and launch with minimal to no configuration.
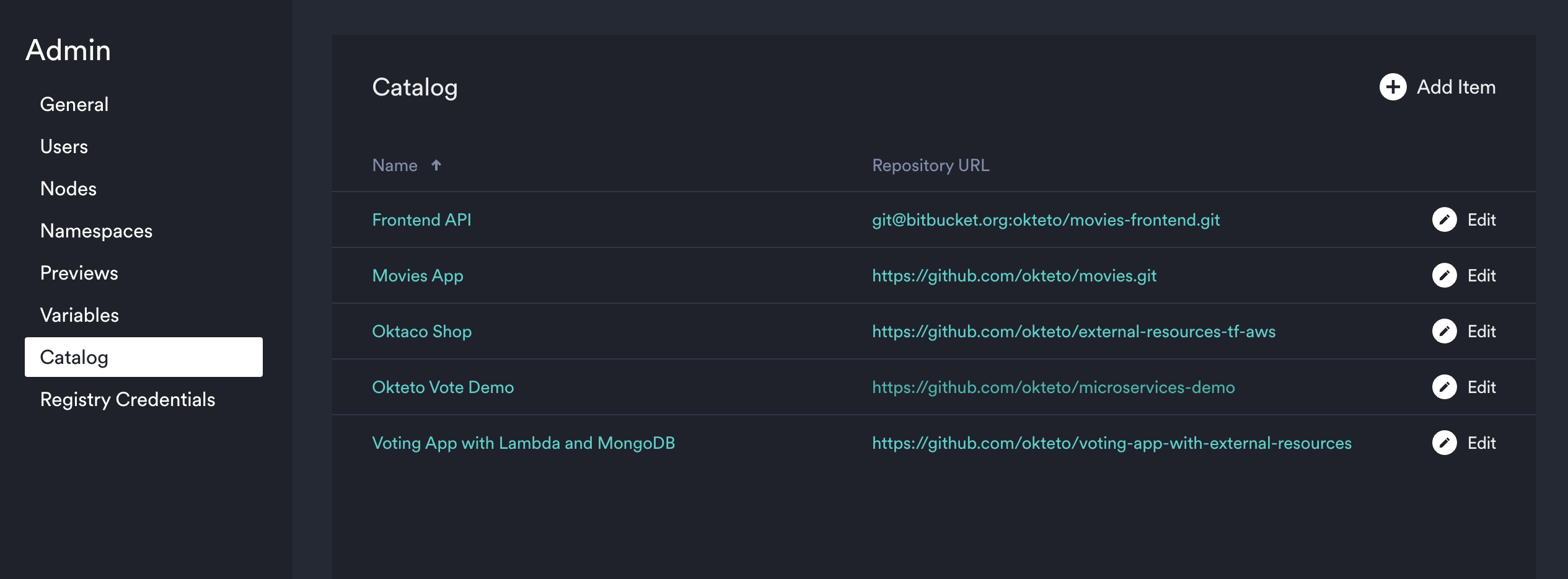
In this view you can see the name, repository URL, and edit any pre-existing catalog entries. Please see our Catalog documentation to learn more about how to modify each field.
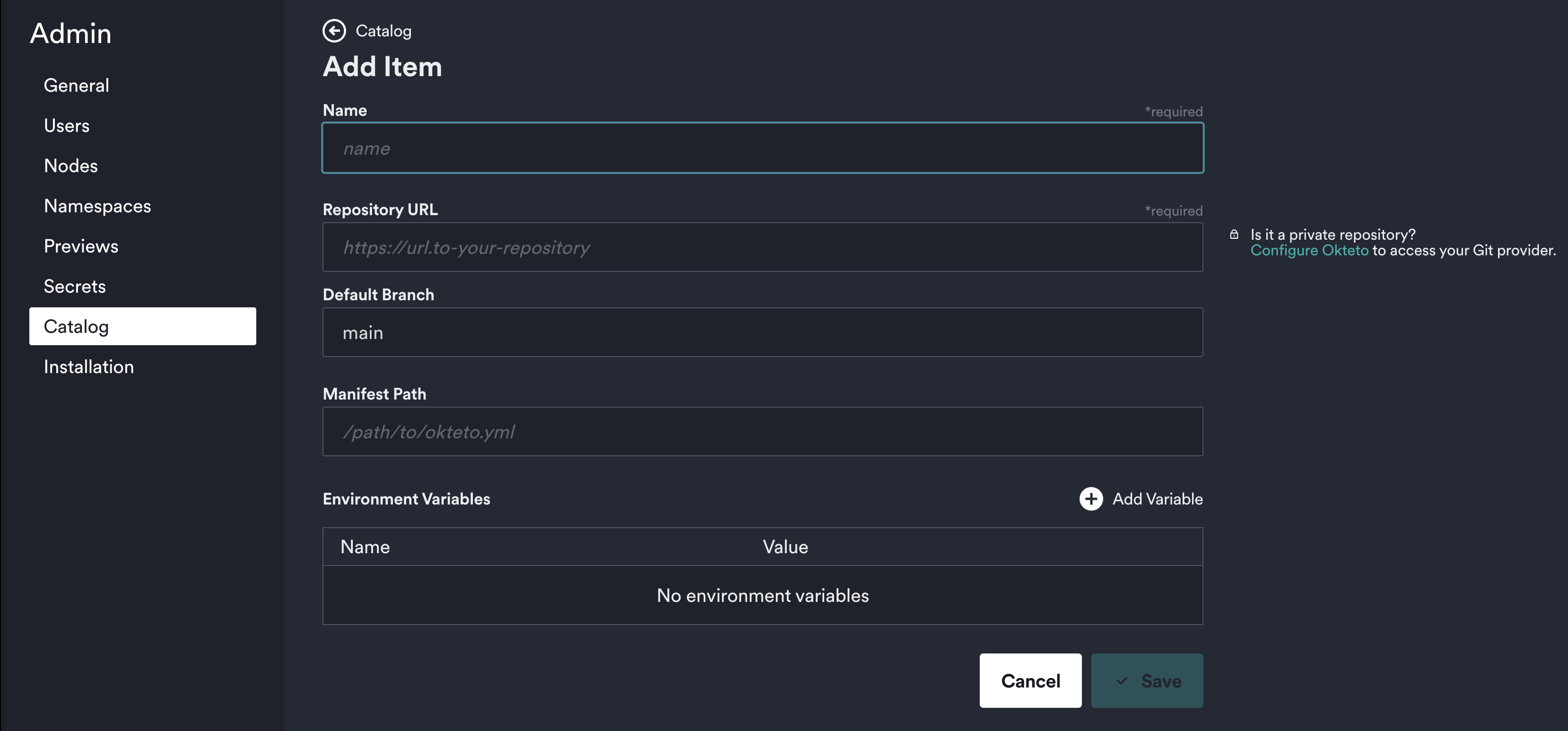
This makes it simple and fast to edit your catalog entries as your environment changes to manage your applications from this central location.
Installation
Okteto is a flexible platform that streamlines your developer operations to make developers faster and more efficient. The initial installation has a few steps and we've built a guided experience to help get you setup even faster than before.
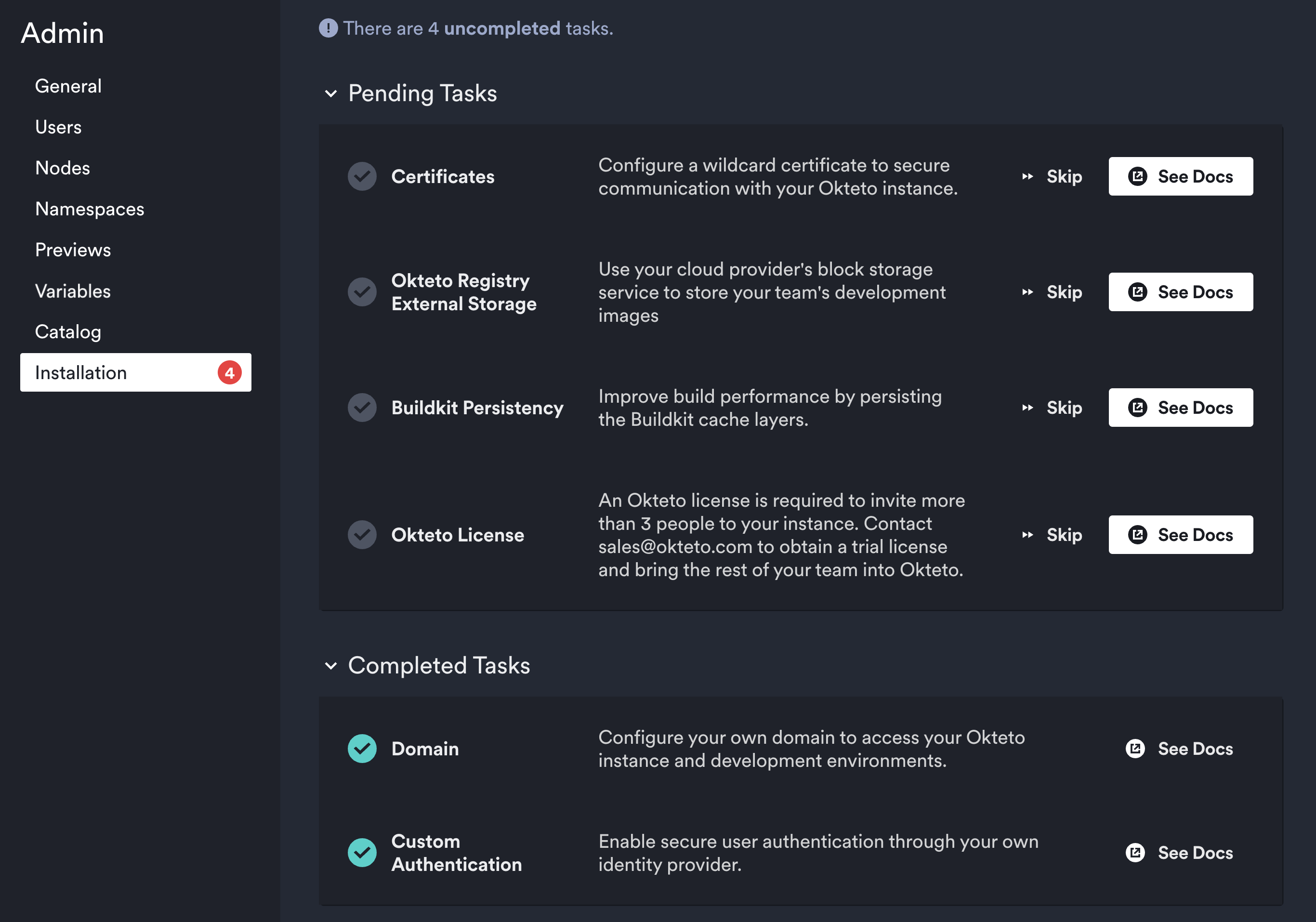
From this page you can follow a simple step-by-step guide to get the major components setup and have your Okteto installation ready to go in minutes. Each of these tasks comes with documentation to help guide you and are also skippable in case they don't apply to you or you simply wish to complete them later.
Registry Credentials
In this section of the Admin dashboard you can manage the private registry credentials for your Okteto instance. The credentials you configure here are injected by Okteto into any operation (e.g. build, deploy) performed by developers so they don't need direct access to the credentials. Once you configure the credentials here all developers in your Okteto instance will be able to use the respective registries while developing with Okteto. You can also manage these credentials directly in your Kubernetes cluster using the CRDs created by Okteto.
If the setting daemonset.configurePrivateRegistriesInNodes.enabled is enabled, Okteto's daemonset will also configure these credentials in the nodes so the cluster can also pull images from those registries.
For each configured registry, you will see a row with the type (Static or AWS) and the registry hostname. The 2 types of credentials supported are:
- Static: Registry configuration using static username and password credentials (e.g. Docker Hub)
- AWS: ECR registry configuration using Access Key and Access Secret. Okteto takes care of refreshing docker credentials every 4 hours using the key and secret configured. The hostname of the registry must end with
.amazonaws.com.
Registries must be included using a valid host name. For example, index.docker.io or 111122223333.dkr.ecr.eu-central-1.amazonaws.com. For static registries, if the registry is exposed in a port other than the default http(s) 80/443 it must be included in the name, eg: my-registry.com:5000
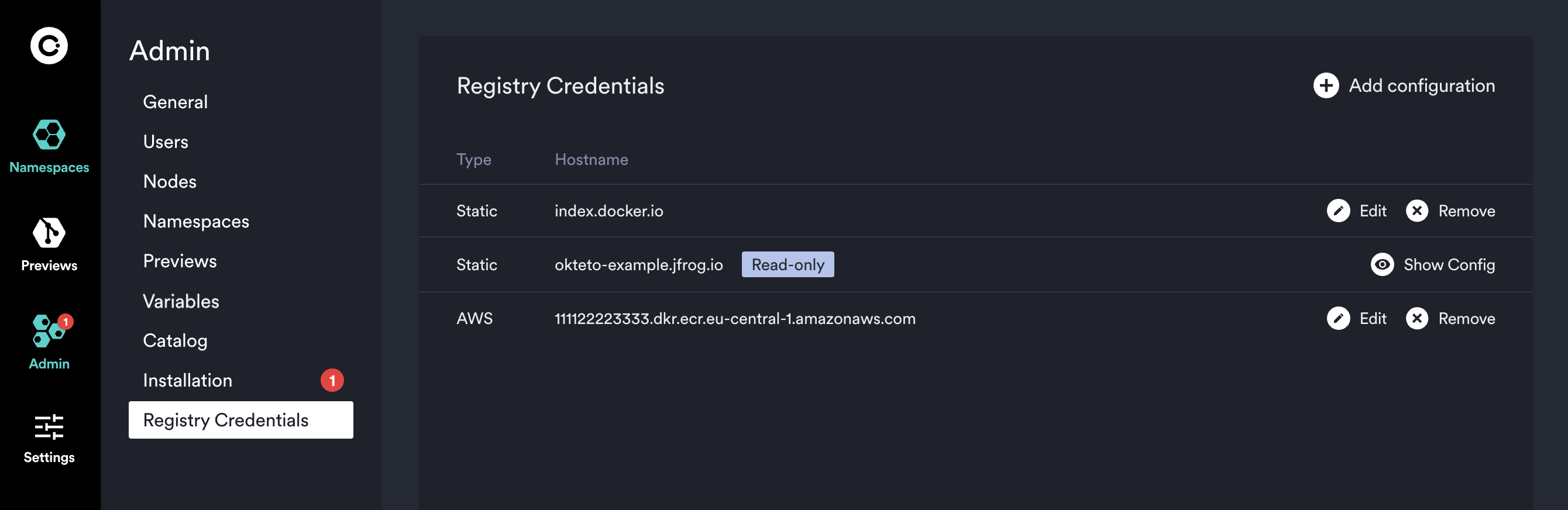
This admin view also enables you to rotate your registry credentials or delete them if you don't need them anymore. For sensitive data you will only see the last few characters as a hint to verify the value.
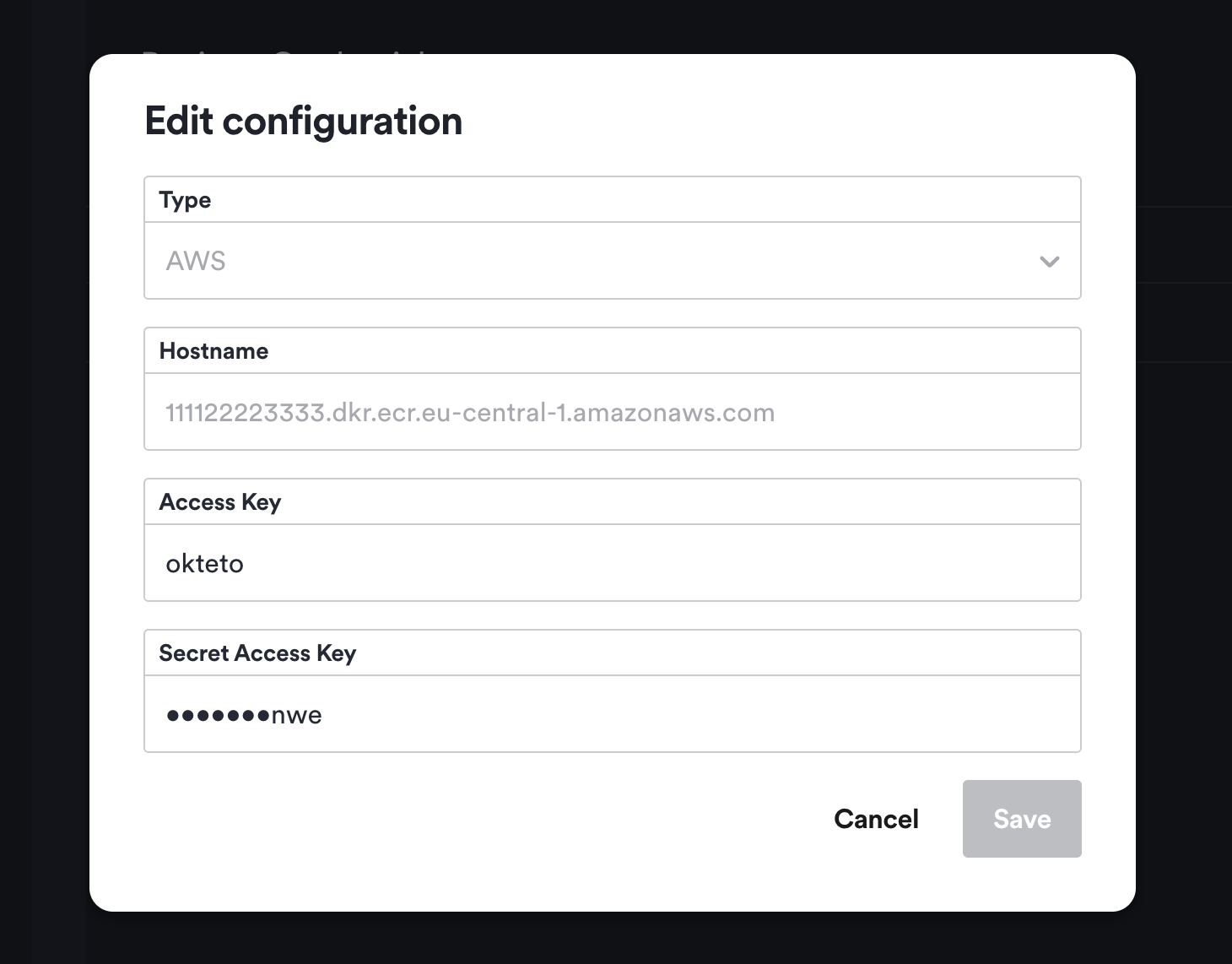
Be aware that any changes you make to credentials may take a few minutes to propagate to all of the components in the cluster.